Device iotlb: Difference between revisions
From KVM
(→Design) |
(→Design) |
||
| Line 14: | Line 14: | ||
* Vhost-net can query the address mappings from io virtual address to userspace address through ioctl. | * Vhost-net can query the address mappings from io virtual address to userspace address through ioctl. | ||
* The above translation result could be cached in vhost for a while to speed up the future translation in the future. | * The above translation result could be cached in a vhost device specific IOTLB for a while to speed up the future translation in the future. | ||
* Qemu can invalidate one or more mappings that cached by vhost through ioctl. | * Qemu can invalidate one or more mappings that cached by vhost through ioctl. | ||
* Qemu can start or stop the DMAR through ioctl. | * Qemu can start or stop the DMAR through ioctl. | ||
[[Image:iotlb.png]] | [[Image:iotlb.png]] | ||
Revision as of 04:02, 4 February 2016
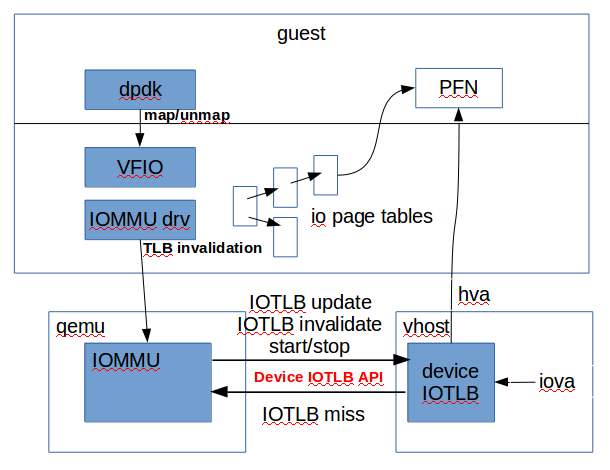
Vhost-net Device IOTLB
Overview
This page provides information about the design of Device IOTLB for vhost-net to provides a secure and efficient environment for dpdk like program in guest.
Design Goals
- Architecture independent: The implementation should be compatible to current Qemu's IOMMU architecture, then it should be architecture independent and then be easy to be ported to various platform/IOMMU implementation.
- Efficient: End user should have no obvious felling performance degradation when using dpdk like program in guest.
- Compatible: The implementation should be compatible to current vhost-net memory region API to support VM without DMAR enabled.
Design
- Vhost-net can query the address mappings from io virtual address to userspace address through ioctl.
- The above translation result could be cached in a vhost device specific IOTLB for a while to speed up the future translation in the future.
- Qemu can invalidate one or more mappings that cached by vhost through ioctl.
- Qemu can start or stop the DMAR through ioctl.